Quick & Easy: Game Client Security Secrets Revealed in 5 Minutes!

Written by BACKND CEO Owen, 13 December 2024
Hello! I'm Owen from BACKND
Ensuring robust security is just as critical to a game's success as having engaging gameplay. Since 2018, we have been managing the game BACKND server and have encountered various hacking attempts. Today, I’m here to share some core insights based on our experience.
This guide is designed especially for indie and small game studios without a dedicated security expert. Your time is precious, so in just 5 minutes, I’ll help you achieve 80% proficiency in client security.
<Game Security Layers: Client, Network, Server>
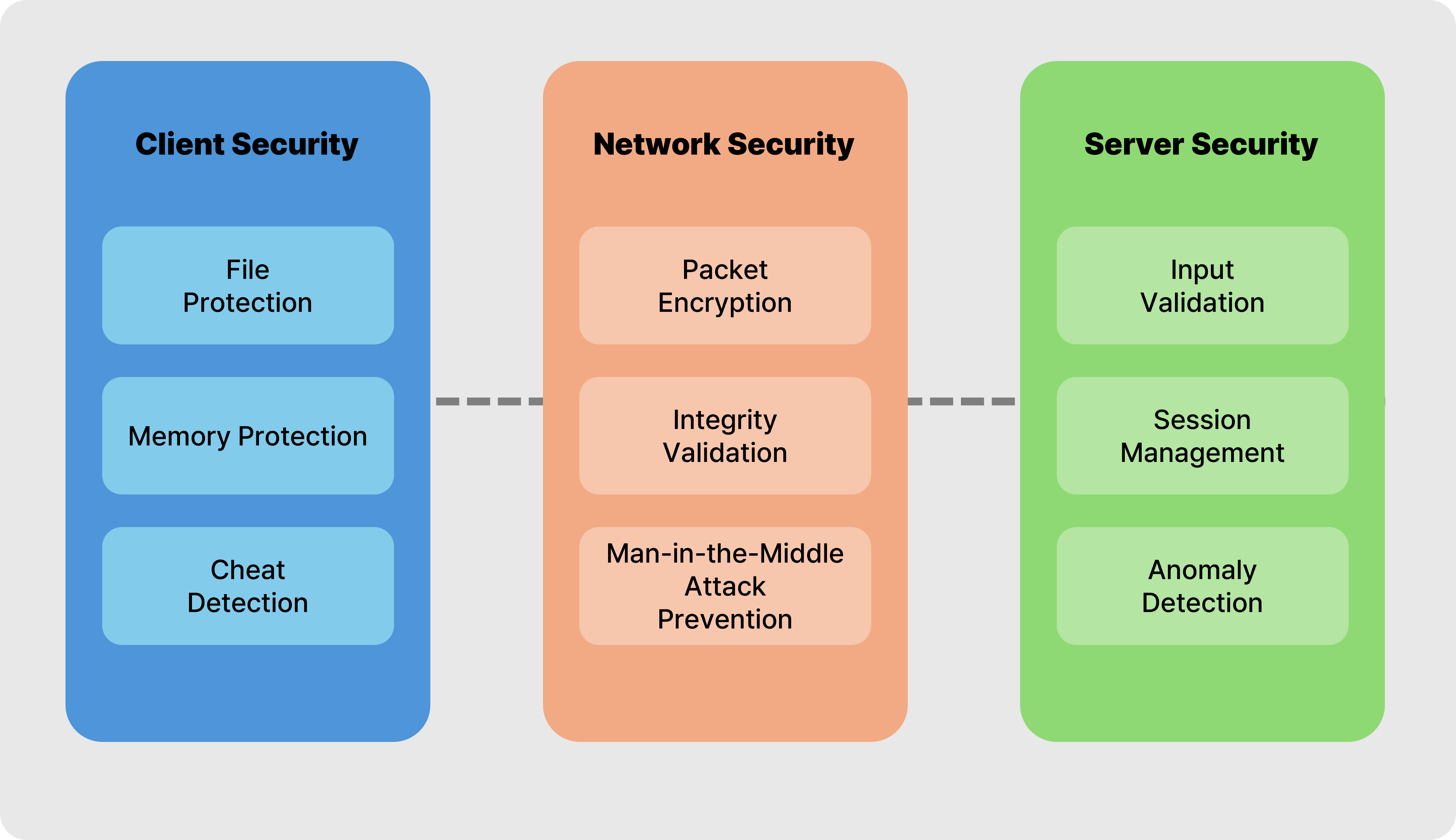
Always keep these in mind! Game security is built on three essential layers ① Client Security → ② Network Security → ③ Server Security
<Security Responsibility by layers>
For server and network security, SaaS solutions like BACKND often include these features as part of their offerings. In the case of BACKND, we’ve designed our platform to ensure that indie and small-scale developers can focus on their games without worrying about server and network security. By using BACKND, you can rest assured that these areas of security are fully managed for you.
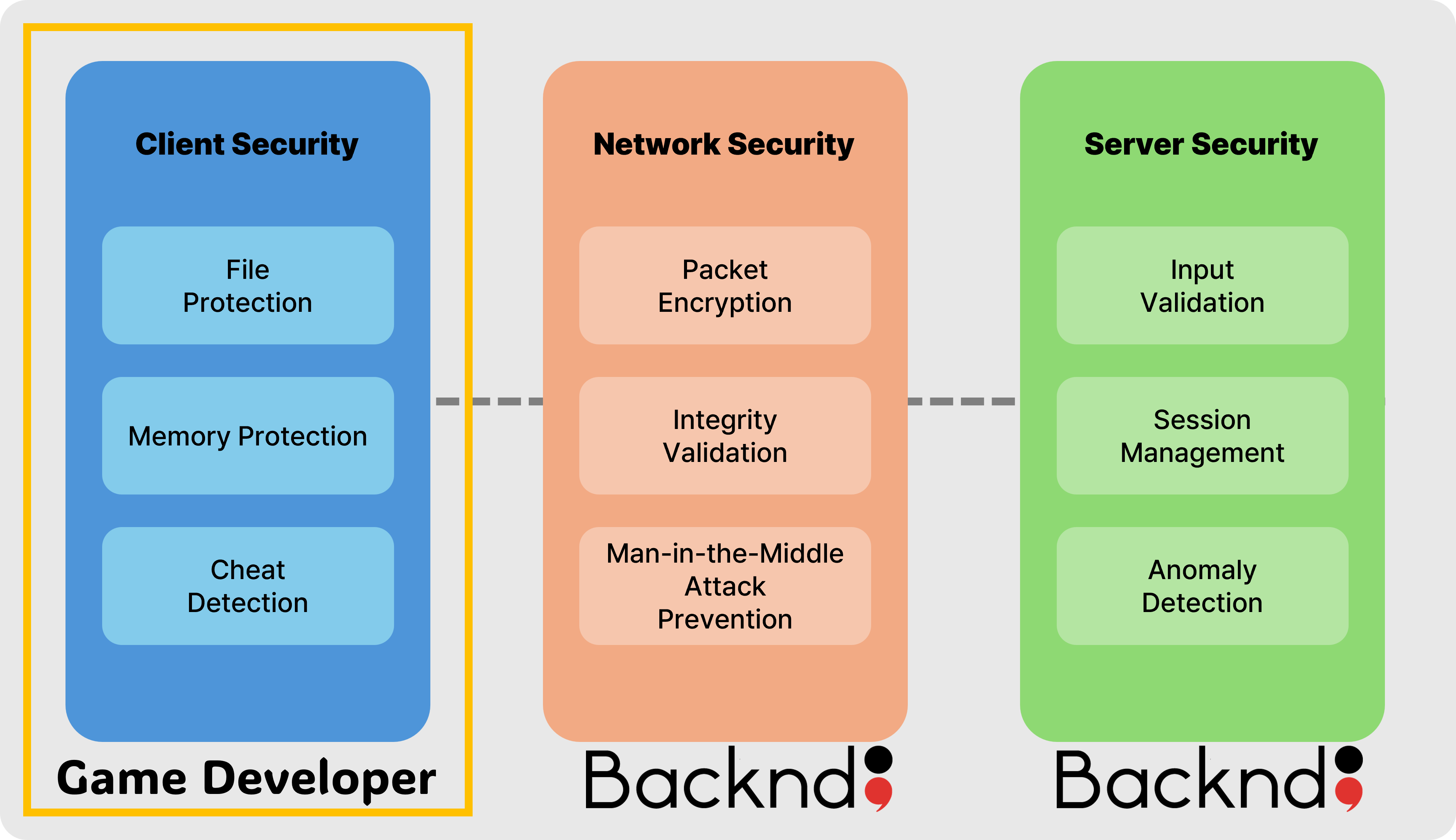
- Client Security
This is your responsibility as the game developer. It’s the area you must focus on defending, which is the main subject of this guide.
<File Security Guide>
Hacking Difficulty: Easy
Game files are the first target for hackers. Data stored locally on smartphones can be easily tampered with, potentially disrupting game balance and revenue streams.
Key Principles
- Minimize Local Storage: Store game data on servers whenever possible.
- Encrypt When Necessary: If local storage is unavoidable, ensure encryption.
Recommended Encryption Algorithms
- Priority 1: AES-256-GCM
- Fast performance
- Includes data integrity checks
- Widely supported libraries
- Priority 2: ChaCha20-Poly1305
- Superior performance in mobile environments
- Simpler implementation
(Note: Algorithm recommendations were aided by Claude 3.5 (Sonnet). These are not from my personal perspective.)
Encryption Key Management
- Correct Method:
- Receive the encryption key from the server at game startup.
- Store it temporarily in memory.
- Delete it from memory when the game ends.
- Incorrect Method:
❌ Hardcoding keys in the client
❌ Storing keys locally
Leverage Cloud Save for Local Storage
If local storage is unavoidable, consider using cloud save services:
<Memory Security Guide>
Hacking Difficulty: Moderate
Memory hacking involves scanning and altering values stored in memory during game execution.
Typical Memory Hacking Process:
- Use tools like Cheat Engine to scan for current values.
- Modify the value in-game (e.g., spending gold).
- Rescan for the updated value.
- Pinpoint memory address.
- Manipulate the value.
Recommended Anti-Memory Hacking Assets
- Anti-Cheat Toolkit 2024
- Link
- Rating: 4.9/5.0
- Price: $80
- Anti Cheat Pro - 2024
- Link
- Rating: 4.7/5.0
- Price: $39.99
<Client Code Security Guide>
Hacking Difficulty: High
Client code, such as APK and IPA files, is vulnerable to decompilation.
- Android: APK files can be converted to Java or Smali code.
- iOS: IPA files can be viewed as ARM assembly code.
Recommended Code Obfuscation Assets
- Obfuscator Pro
- Link
- Rating: 4.4/5.0
- Price: $79.88
- Mfuscator: IL2CPP Encryption
- Link
- Rating: 4.8/5.0, 150K+ downloads
- Price: $79.99
<Tip 1: Efficient Data Storage Strategies>
Managing all data changes through the server enhances security, but it can also be costly. To balance safety and cost, we recommend the following strategies:
- Classify Data by Importance
- Critical Data: Store immediately
- Changes in premium or cash-based resources
- Acquisition or usage of premium items
- Key item enhancement events
- Job changes or evolution events
- Gacha or loot box systems
- Account information changes
- General Data: Store every 15–30 minutes
- Standard resources (e.g., idle gold)
- Game progress updates"
<Tip 2: Use Serverless Functions for Critical Data Management>
Critical data is safer when created and managed on the server. If you have some experience or understanding of server development, you can easily implement and manage this logic using serverless functions.
We recommend services such as AWS Lambda, GCP Cloud Functions, or Azure Functions for implementing serverless logic.
If you're using BACKND, you can easily implement and manage this logic with BACKND Functions, the serverless function solution provided by BACKND.
- AWS Lambda
https://aws.amazon.com/lambda/ - GCP Cloud Functions
https://cloud.google.com/functions?hl=en - Azure Functions
https://azure.microsoft.com/en-us/products/functions - BACKND Functions (serverless functions provided by BACKND)
BACKND Functions | BACKND
In Conclusion
Your five minutes are up! In this guide, we quickly covered the core areas of game client security, including ① file encryption, ② memory encryption, ③ code obfuscation, and ④ managing critical variables on the server. With just a bit of effort, these techniques can provide over 80% effectiveness in securing your game.
We wish you success in delivering a secure game that players will love and that thrives commercially! :)
(Next Topic Preview)
In our next guide, we’ll cover 'Essential Game Security Checklist Before Launch(TBD)'.
- A comprehensive pre-launch security checklist
- Must-have security features
Stay tuned! 😉
If you like this posting, please subscribe us!

© 2024 AFI, INC. All Rights Reserved. All Pictures cannot be copied without permission.
![[External Essay] Gamescom 2025 Interactions](/content/images/size/w600/2025/09/------1.png)


